#parsing email headers
Explore tagged Tumblr posts
Text
Supercharging Jira Cloud with Forge Services: A Look Through Sparxsys Solutions
In the world of agile teams and modern project management, Jira Cloud has become a cornerstone tool for collaboration, task tracking, and workflow automation. But with every versatile platform comes the need for customization—and that’s where Jira Forge shines.
With Forge, Atlassian provides a cloud-native development platform that enables developers to create secure, scalable, and reliable apps right within the Jira ecosystem. Among Forge’s most powerful features are Forge Services, which help developers interact with Jira's APIs, manage storage, call external APIs, and more—all while keeping performance and security in check.
In this post, we’ll explore how Jira Forge Services can transform your Jira experience, and we’ll look at how companies like Sparxsys Solutions are leveraging this technology to build real-world apps that solve specific business problems.
What Are Jira Forge Services?
Atlassian Forge Services are a collection of pre-packaged modules that simplify tasks such as:
Storing data (@forge/storage)
Calling remote APIs (@forge/api)
Authenticating with third-party systems (@forge/oauth)
Fetching information from Jira itself (@forge/jira)
These services eliminate the need to set up separate backend infrastructure. Everything runs in Atlassian’s secure cloud, which means no separate servers or databases to maintain.
This serverless model greatly reduces development complexity and security risks, making Forge the ideal platform for small and enterprise teams alike.
Why Use Forge Services?
Whether you’re building an internal Jira app for your organization or creating a marketplace app for global users, Forge Services offer some clear benefits:
Security by Design: Forge apps operate within Atlassian’s security sandbox, so you don’t have to worry about common vulnerabilities like SQL injection or cross-site scripting.
Simplified Development: With built-in services like @forge/api, calling the Jira REST API becomes a breeze. No need to handle authentication headers manually.
Scalability: Since the apps run in the cloud, they scale automatically based on demand.
Low Maintenance: Forge handles hosting, security, and patching, which reduces the overhead for developers.
Real-World Implementation: Sparxsys Solutions
One of the standout players in the Atlassian ecosystem is Sparxsys Solutions, a leading consultancy that specializes in Jira, Confluence, and Atlassian app development. Known for their contributions to the Atlassian Marketplace and strong community presence, Sparxsys has been at the forefront of leveraging Forge Services.
In one of their recent projects, Sparxsys developed a custom Forge app to help a client automate Jira issue creation based on incoming emails from a specific service. Using Forge’s API and storage services, they created an app that:
Listens to email events via a webhook
Parses the email content
Extracts relevant information
Creates a Jira issue automatically with all required custom fields
All of this was done without deploying a single server. The result was a lean, maintainable, and highly scalable solution that was delivered in record time.
A Glimpse at the Code
Here’s a simple example of how @forge/api can be used in a Forge app to fetch Jira issues:
javascript
CopyEdit
import api from '@forge/api'; export async function run() { const response = await api.asApp().requestJira('/rest/api/3/search?jql=assignee=currentUser()'); const data = await response.json(); console.log(data); }
In just a few lines, developers can interact with Jira data securely and efficiently. No tokens, no auth headaches—just clean, direct API access.
What About Forge Limitations?
Forge is still evolving, and there are a few limitations developers should be aware of:
Not all Jira REST API endpoints are currently supported.
Timeouts can affect long-running processes.
Limited ability to run background jobs (though Atlassian is improving this with scheduled triggers).
That said, Forge is gaining features rapidly, and the benefits of serverless architecture often outweigh these limitations for many use cases.
Final Thoughts
Jira Forge Services represent a major leap forward in Atlassian app development. They offer a blend of security, scalability, and simplicity that’s hard to match with traditional app frameworks. By offloading infrastructure concerns, Forge lets developers focus purely on creating value.
Companies like Sparxsys Solutions are already building innovative, real-world solutions on this platform—and that’s just the beginning. Whether you're a seasoned Jira admin or a developer looking to break into the Atlassian ecosystem, now is the perfect time to explore what Forge Services can offer.
Want to get started? Visit the Forge Developer Hub and start building your first app today.
0 notes
Text
Lab 10: Binary File Parsing & Email Lookup in C
QUIZ: print_department.c ======================== First, review the print_department.c file, as many of the techniques it demonstrates will need to be used to complete this lab. Near the top of the program ‘print_department.c’, code like the following appears. ,—- | file_header_t *header = (file_header_t *) file_bytes; `—- Which of the below best describes what this line is doing? – (X) It sets a…
0 notes
Text
Parse Emails in Browser & Serverless: postal-mime
postal-mime is a JavaScript library that parses RFC822 email messages directly in browsers and serverless environments. It transforms raw email data into structured JavaScript objects containing headers, recipients, attachments, message content, and more. More Features: Can be run in Web Workers to avoid blocking the main thread. Runs in serverless platforms like Cloudflare Email…
0 notes
Text
How to Create an Effective Resume
How to Create an Effective Resume
In this guide, you’ll learn how to create an effective resume. You’ll discover strategies for tailoring your resume to the role you’re pursuing and learn how to effectively present your skills and experience—whether you’re a new job seeker or a mid-career professional switching to a new field. You'll understand the structure of every core section of a successful resume, and explore various templates and formats. Download this guide in PDF format
Strategy
An effective resume needs to present all the important information about you as a professional in a concise and clear way. Format and content are both important. Before diving into the details of resume structure, have a clear understanding of what you are trying to communicate. Focus on what matters to the employer and tailor your resume to the role.
Focus on What’s Important to the Employer
Before writing your resume, consider the employer’s point of view. What do they want to know? Answering this question helps you focus on the relevant information, increasing your chances of getting their attention. Carefully read the job description to understand what the employer is looking for. If possible, review multiple job descriptions to see what requirements appear repeatedly. Networking with industry professionals can also provide valuable insights.
Tailor Your Resume to a Role
It’s essential to tailor your resume to each job you apply for. Even if the roles have similar requirements, adjust the order of your qualifications to match the job description. Use the employer’s terminology to help them relate to you and to avoid being filtered out by automated software that relies on keywords.
Different Types of Job Seekers
Your resume strategy will differ depending on your career stage. New professionals and career changers need to communicate their value despite lacking direct experience in the field. Focus on transferable skills and highlight relevant experiences. For career changers, adopt the terminology of your new industry.
New Professionals
If you lack professional experience, leverage non-professional experiences such as coursework, extracurricular activities, volunteer work, and life experiences. Use sections like Projects, Volunteer Work, and Relevant Experiences as alternatives to Professional Experience.
Templates and Layouts
Design your resume using an existing template or create your own. There are many templates available online. Choose one that ensures ease of reading and a simple design that can be easily parsed by both humans and applicant tracking systems (ATS). Keep your resume to one page unless you have 10-15 years of relevant experience.
Resume Sections
Before filling out your resume, decide which sections to include and in what order. Core sections should include Contact Information, Professional Summary, Skills, Experience, and Education. Optional sections could include Projects, Publications, Volunteer Experience, Awards and Honors, Patents, Languages, and more.
Header
This section at the top of your resume includes your contact information. Your name should be in a larger font. Include your city, state, zip (no street address), phone number, email address, LinkedIn profile URL, and optionally a personal website, GitHub (for technical roles), or portfolio (for creative roles).
Summary
Located immediately after the header, the Summary should be brief (3-5 lines) and clearly articulate what makes you a great candidate for the role. Describe yourself by role and competencies, connect your expertise to your value proposition, and include a differentiator.
Skills
List your core areas of expertise and specific skills. For non-technical roles, include 4-8 short bullets detailing quantifiable skills. For technical roles, list all relevant technical skills and organize them by type if necessary.
Professional Experience
This section should list your roles in reverse chronological order, including company, job title, location, and employment dates. Detail your responsibilities and accomplishments for each role, using numbers to show the scope and impact of your work. Avoid chronological gaps and explain any significant time out of the workforce.
Education
List degrees beyond high school in reverse chronological order, including degree, institution, location, and date of completion. Include pending or incomplete degrees by marking them as “In progress” or “Incomplete.”
Finalize Your Resume
Have someone proofread your resume for typos and consider feedback from trusted individuals familiar with your work. Remember, your resume is a living document that can be revised based on feedback.
Use this guide to create an effective resume that avoids common problems and pitfalls. Focus on your skills and experience, present yourself in the best light possible, and get ready to land that next role!
We're a job placement agency with lots of job opportunities every day. We work with over 1000+ companies. Join us, and we'll make sure you receive job alerts that match your profile., you can directly apply. Best part? It's all free. No fees involved. Join us today! Best of Luck.
Official Website: https://jobshiringopen.com/
Join our HR team:
WhatsApp: [https://whatsapp.com/channel/0029Vab4T7p7Noa6aDI0nE0M] Telegram: [https://t.me/jobshiringopen] Linkedin: [https://www.linkedin.com/company/jobhiringopen/]
Regards, HR – JobsHiringOpen.com
1 note
·
View note
Text
Cover Letter Examples - Essential Job Hunting Tools
If discover you're mailing resume after resume at the same time phone still isn't ringing it's missing a competitive advantage. What your resume needs for you to clearly show the hiring manager who you are, why you're issue at utilising do and how you're in order to be meet requirements. You have to peak the hiring manager's interest enough to provide a oceanfront call and below are several reasons why your resume isn't quite making the cut.
Once your email is clicked on make sure your resume is attached in Word Format-most Applicant Tracking Systems (ATS) parse your Resume Optimization information incredibly easier if moment has come in Phrases.
Keep it simple, relating to a many solutions. Don't include graphics, logos or pictures. Also, don't test and get fancy with text boxes, headers or footers. While resume-parsing tools are a fantastic Job Search Optimization resource and save hours upon hours of manual data entry, they can't always parse text boxes, headers or footers with 100 percent accuracy. It's good to avoid associated with and take out these features altogether. Furthermore, almost all ATS will strip down resumes into their most basic format, text only. So don't stress over font or color - sooner or later it doesn't matter.

youtube
Then and than are worried immediately. Then indicates an event to follow as in "then we crossed the finish line". Than is an assessment word including "Bill is larger than George". They don't mean factor thing, along with many people all of them confused. This is just one tyoe of poor sentence structure. If you are not sure, use your built in checker or read one another loud alone. But by all means are right before putting it to the police.
The description meta tag appears in the html programming code in "head" tag and just underneath the "title" tag. This site description supplies a summary in the the page is heading towards the search engines. While the page title is short, ranging from couple of words ATS Friendly Checker a few short sentence, the page description may range from a single sentence a few short paragraph. This description might be used as the description of your web page in the search engine's search dividends. "Might" is the operative word, because in some cases the description is used and additionally the web presence grabs a description from elsewhere on the page - depending, in part, exactly how to relevant it determines your description become.
What do you see possess Google company is? Do you should click through several pages before discover your company's website? Consider if you Google your products? If you can't locate your company coming up in a favorable way, you'll want to do some organic search engine marketing.
From here, it is your job to show visitors into conversions. Introduced finding compelling ways to get the searcher's attention from the minute they find your page and keeping them click-through to something. Extra click-throughs you get, today, the contemporary your rank will take full advantage of.
The ambiguity of resume cover letters. For some organizations, though not all, could possibly only upload ONE job application letter regardless of how many jobs within that company you ultimately want to apply to. If this is the case, you should include a generic cover letter that would atsfriendly.com cover your bases virtually any role during that company, not for an actual position. There is no golden rule on this one, though, and you should consider if you're applying for one job or several at the same organization, so it is simply something to comprehend. And if you just aren't sure, ask!
1 note
·
View note
Text
Enabling CSV data uploads via a Salesforce Screen Flow
This is a tutorial for how to build a Salesforce Screen Flow that leverages this CSV to records lightning web component to facilitate importing data from another system via an export-import process.
My colleague Molly Mangan developed the plan for deploying this to handle nonprofit organization CRM import operations, and she delegated a client buildout to me. I’ve built a few iterations since.
I prefer utilizing a custom object as the import target for this Flow. You can choose to upload data to any standard or custom object, but an important caveat with the upload LWC component is that the column headers in the uploaded CSV file have to match the API names of corresponding fields on the object. Using a custom object enables creating field names that exactly match what comes out of the upstream system. My goal is to enable a user process that requires zero edits, just simply download a file from one system and upload it to another.
The logic can be as sophisticated as you need. The following is a relatively simple example built to transfer data from Memberpress to Salesforce. It enables users to upload a list that the Flow then parses to find or create matching contacts.
Flow walkthrough
To build this Flow, you have to first install the UnofficialSF package and build your custom object.
The Welcome screen greets users with a simple interface inviting them to upload a file or view instructions.

Toggling on the instructions exposes a text block with a screenshot that illustrates where to click in Memberpress to download the member file.
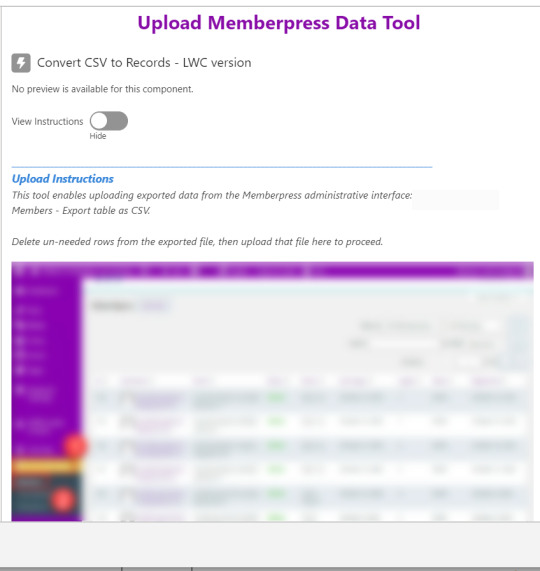
Note that the LWC component’s Auto Navigate Next option utilizes a Constant called Var_True, which is set to the Boolean value True. It’s a known issue that just typing in “True” doesn’t work here. With this setting enabled, a user is automatically advanced to the next screen upon uploading their file.
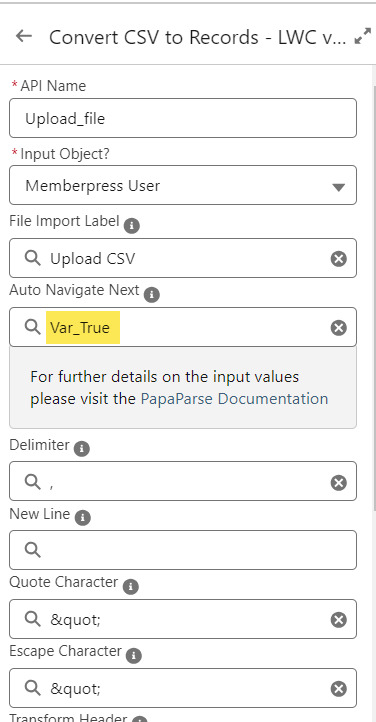
On the screen following the file upload, a Data Table component shows a preview of up to 1,500 records from the uploaded CSV file. After the user confirms that the data looks right, they click Next to continue.
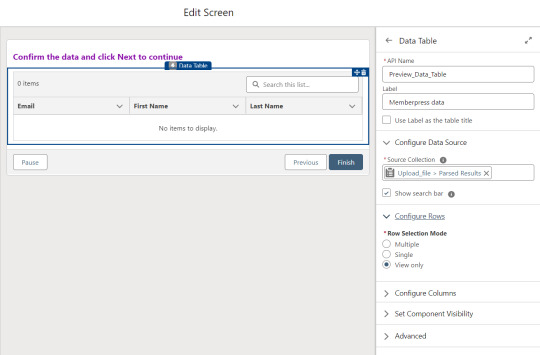
Before entering the first loop, there’s an Assignment step to set the CountRows variable.

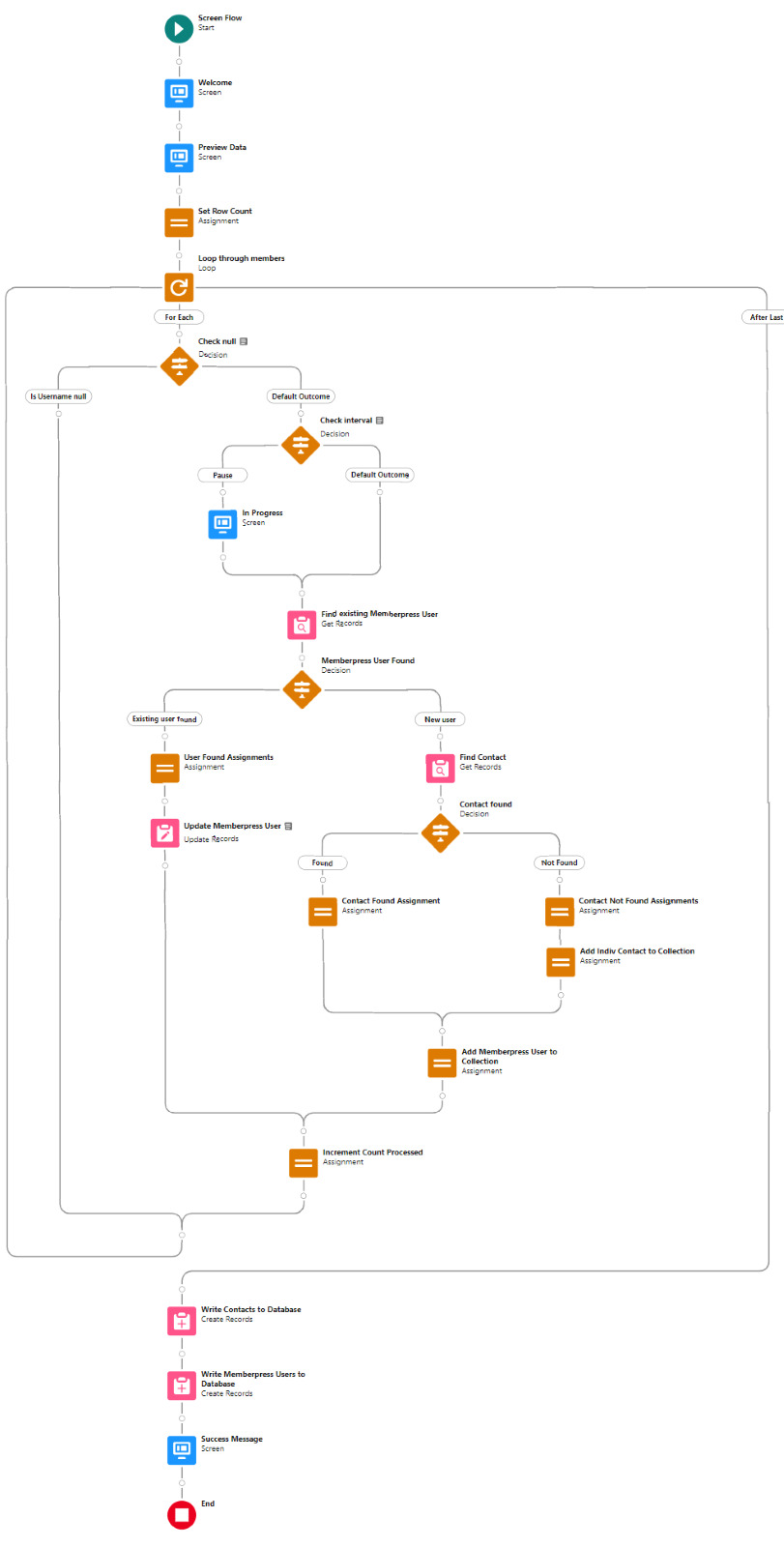
Here’s how the Flow looks so far..

With the CSV data now uploaded and confirmed, it’s time to start looping through the rows.
Because I’ve learned that a CSV file can sometimes unintentionally include some problematic blank rows, the first step after starting the loop is to check for a blank value in a required field. If username is null then the row is blank and it skips to the next row.

The next step is another decision which implements a neat trick that Molly devised. Each of our CSV rows will need to query the database and might need to write to the database, but the SOQL 100 governor limit seriously constrains how many can be processed at one time. Adding a pause to the Flow by displaying another screen to the user causes the transaction in progress to get committed and governor limits are reset. There’s a downside that your user will need to click Next to continue every 20 or 50 or so rows. It’s better than needing to instruct them to limit their upload size to no more than that number.

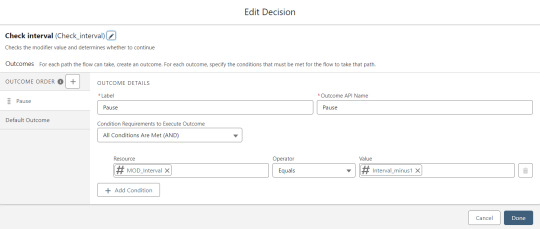
With those first two checks done, the Flow queries the Memberpress object looking for a matching User ID. If a match is found, the record has been uploaded before. The only possible change we’re worried about for existing records is the Memberships field, so that field gets updated on the record in the database. The Count_UsersFound variable is also incremented.

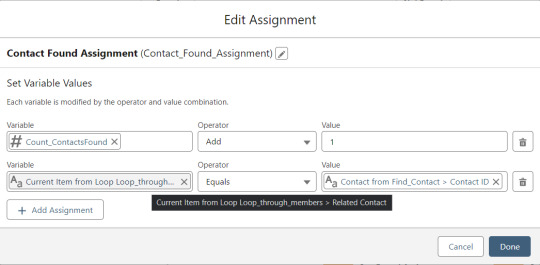
On the other side of the decision, if no Memberpress User record match is found then we go down the path of creating a new record, which starts with determining if there’s an existing Contact. A simple match on email address is queried, and Contact duplicate detection rules have been set to only Report (not Alert). If Alert is enabled and a duplicate matching rule gets triggered, then the Screen Flow will hit an error and stop.

If an existing Contact is found, then that Contact ID is written to the Related Contact field on the Memberpress User record and the Count_ContactsFound variable is incremented. If no Contact is found, then the Contact_Individual record variable is used to stage a new Contact record and the Count_ContactsNotFound variable is incremented.


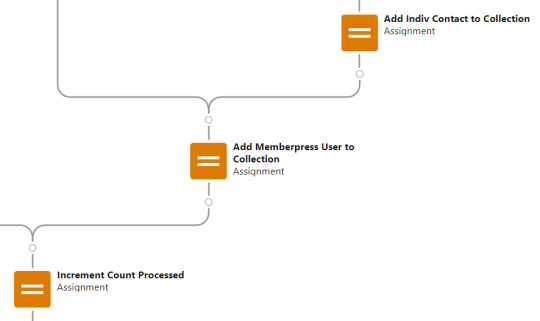
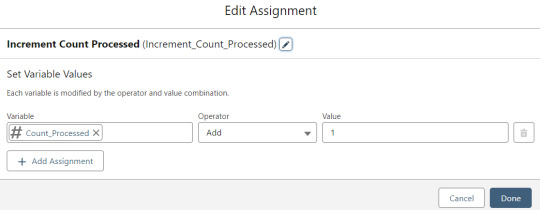
Contact_Individual is then added to the Contact_Collection record collection variable, the current Memberpress User record in the loop is added to the User_Collection record collection variable, and the Count_Processed variable is incremented.


After the last uploaded row in the loop finishes, then the Flow is closed out by writing Contact_Collection and User_Collection to the database. Queueing up individuals into collections in this manner causes Salesforce to bulkify the write operations which helps avoid hitting governor limits. When the Flow is done, a success screen with some statistics is displayed.
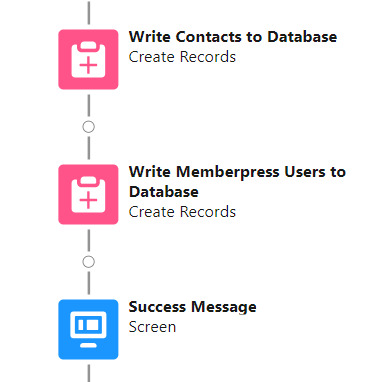

The entire Flow looks like this:
Flow variables
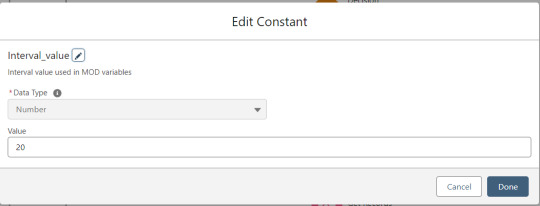
Interval_value determines the number of rows to process before pausing and prompting the user to click next to continue.
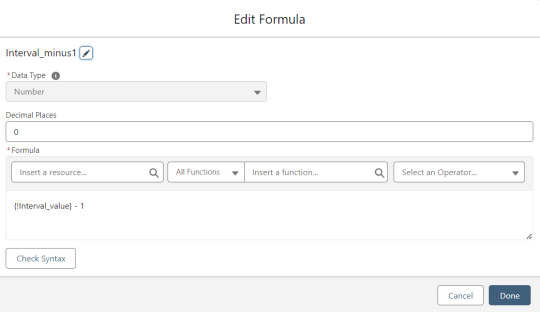
Interval_minus1 is Interval_value minus one.
MOD_Interval is the MOD function applied to Count_Processed and Interval_value.

The Count_Processed variable is set to start at -1.

Supporting Flows
Sometimes one Flow just isn’t enough. In this case there are three additional record triggered Flows configured on the Memberpress User object to supplement Screen Flow data import operations.
One triggers on new Memberpress User records only when the Related Contact field is blank. A limitation of the way the Screen Flow batches new records into collections before writing them to the database is that there’s no way to link a new contact to a new Memberpress User. So instead when a new Memberpress User record is created with no Related Contact set, this Flow kicks in to find the Contact by matching email address. This Flow’s trigger order is set to 10 so that it runs first.
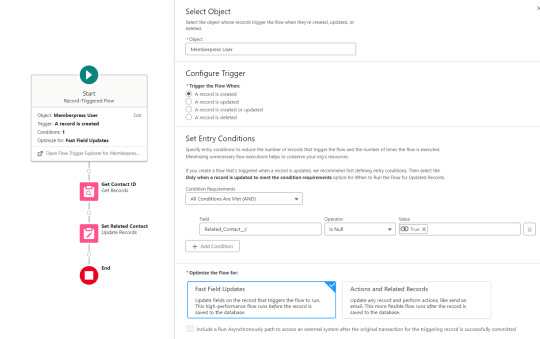
The next one triggers on any new Memberpress User record, reaching out to update the registration date and membership level fields on the Related Contact record

The last one triggers on updated Memberpress User records only when the memberships field has changed, reaching out to update the membership level field on the Related Contact record


0 notes
Text
MHA - Mail Header Analyzer
MHA - Mail Header Analyzer #Mail #Header #Analyzer #MHA #Hacking #flask #headers
Mail header analyzer is a tool written in flask for parsing email headers and converting them to a human readable format and it also can:
Identify hop delays.
Identify the source of the email.
Identify hop country.
MHA is an alternative for the following:
Name Dev Issues MessageHeader Google Not showing all the hops. EmailHeaders Mxtoolbox Not accurate and slow. Message Header Analyzer
View On WordPress
#Bind#Docker#email#email headers#flask#Header#Identify the source of the email#of the email#parsing email headers#source of the email
0 notes
Text
OWASP - XSS Attacks
It’s important to understand the reason as to why these sort of attacks are possible and what it all boils down - mixing ‘data’ and ‘control’. XSS attacks rely on the fact that web pages served in our browser (i.e. serving data) are also able to run programs at the same (i.e. control). This is achieved through Javascript - the simple “<script></script>” tags embedded within the markup allow an attacker to run malicious code. This means they can potentially:
Modify user cookies - steal sessions, modify data, etc
Read and change browser DOM
Make XMLHttpRequests in the background to send off and receive data
Potentially fiddle with new HTML5 APIs involving webcam, location and file system
Non-Persistent Attacks
The first class of these attacks are non-persistent; they essentially involve serving up a web page which contains the malicious scripts. This can occur when a user enters data into a form which is reflected back to them, without sanitising the input. They also commonly occur when clicking on links through emails or forums; the link will actually go to the correct site, but will execute a script on the side.
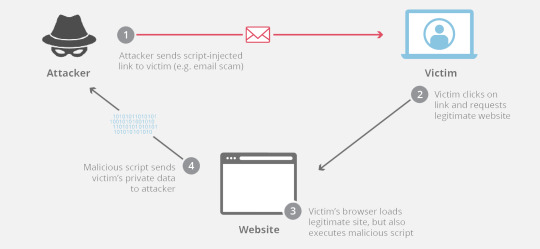
Persistent Attacks
These are the more commonly used and impactful attacks; they rely on a failure of servers to sanitise inputs in forms from Javascript code which results in distributing malicious code to users. For example, let’s say Bob is a regular contributor on the forum SecurityWorld, where you can chat about all things security! After an attack earlier this year, the owner had ramped up security and written a nifty script to parse out any SQL expressions in user input; however it was crappy and hardcoded.
Hacker Mallory comes along and hates the fact that people are spreading ‘useful ways to protect yourself’ when it comes to security; she decides she wants to break into Bob’s account and spread misinformation. The first thing she does is send a DM to Bob; however Mallory is very knowledgeable on XSS attacks and includes a script inside her message. The script fetches all the cookies in the browser and uploads them to a website at www.malloriescookiefactory.com.
The web server doesn’t see anything suss in the input and stores the message in the database. The next time Bob logs in, he accesses the message - the web page then serves him the page with the script included. All his cookies are uploaded to Mallory’s website - Mallory is then able to hijack his session and spread misinformation about the forum.
Protecting Against XSS Attacks
You can find more detailed methods of preventing against XSS attacks in the OWASP cheat sheets here and here. I will summarise the 3 basic concepts however in these protections:
Escaping - rewrite inputs in such a way that nothing is executed if they are served to a user
Validating - prevent special character inputs in forms unless necessary
Sanitising - similar to escaping, except completely removing the problematic characters
In terms of protecting the cookies from being hijacked there are also a number of steps that can be taken as well:
Enable HttpOnly attribute - cookies only submitted to domain of origin
Use Secure attribute - cookies only sent over secure channels
X-XSS protection response headers - feature in the header which prevents pages from loading when they detect an XSS attack
HTTP content security policy headers - allows you to define what and where resources can be loaded from
I also gave a sample attack on HackThisSite - Realistic #9; however the domain used in the injection was fake and only to show the concept.
10 notes
·
View notes
Text
Make You Attractive Resume Format With Best Online Tools 2019
Despite a handful of degrees, you get rejected for a job. Despite a good work experience, you are not even called for a job seeing the resume. Have you ever thought why? The answer to this question is how inviting your resume is? Resume is a window to the self of the candidate. It is a document that not only provides the basic information of the candidate but also creates a drive to meet that candidate and know his further details. A lot of important things around the globe in 5 seconds. For a job seeker, it is imperative to know that there is something most relevant to them that happens in just 5 seconds. It is the scrutiny of the resume. A recruiter can get through your CV is just five seconds or less to decide whether to call you for the interview or not. Here comes the role of a proper Resume Format. Recruiteze offer best resume formatting by dint of iReformat by working through the following available online tools:
· Boundless Resume Templates
iReformat customizes your resume by using unlimited templates used to format the resume. It helps to create a number of combinations that you can opt from in order to suit your resume as per your job requirements. These inbuilt yet customisable templates make it convenient oft a jobseeker to present the information in the best possible layout as desired by the company.
· Limitless Email Templates
Apart from providing ready to use as well as customised templates for resume, it also customises email templates centred around your branding predilections. This tool makes the work easy to go.
· Accurate and Brief Description
It is another important tool in resume formatting wherein iReformat not only manages the document but also ensures a precise and correct parsing of the information which in turn saves time and focusses on quality as well. This formatting in turn makes the resume so impactful that the reader can get through the details in less than five seconds.
· Adaptable Formats
It provides the user with downloadable finished products in a multiple formats such as Microsoft docx, PDF and txt. This tool gives an easy user interface. The jobseeker as well as the recruiter can download the resume and keep it saved with them in the required
· Custom Headers and Footers
Another useful tool is the custom header and footer where the required information such as candidate, recruiter, company name, logo, confidentiality statement, date, page number contact info etc. can be displayed as per customization.
· Customize Sections and Margins
This tool enables the proper formatting of fonts and styles of the employer names, job titles and education. Moreover, the left, right, top and bottom margins are also set through this which looks perfectly fit to size. Recruiteze tries its level best to customise the format in the most readable and acceptable form.
· Format Tables and spaces
The table formatting including its borders, sizes, cell alignment and spacing is done through this tool. This makes the resume more specific and readable. The more formatted through tables and spacing, the more it becomes memorable.
· Applicant’s Information Subdual
The resume formatting not only requires set pattern for adding but also for erasing the non-usable information. This tool helps in hiding or totally erasing the information and photos of the candidate automatically as per the set criteria. This makes it easier for the user to reformat the resume.
· Addition of Watermarks
This is an essential feature which helps to protect the intellectual property of your candidate by adding watermarks as and when needed on the face of the resume.Had there been the absence of this tool the authenticity maintenance of the confidential and important information of the candidate database might not have be on the safer edge.
· Highlight Expertise and Division
This tool provides the most weightage to the most essential information by highlighting the information thereby making the information more eye-catchy.The resume formatting so done by doing the font styling, list styling, content alignment, highlighting the content, marking the sections and divisions etc. automatically proves the benefit of this tool.
Conclusion
In a nutshell, we can say that CV format is truly the way to reach the job interview. Therefore, it needs to be apt as per the requirement of the job. There are wonderful online tools available in the ongoing year 2019 for the purpose of resume formatting. Recruiteze is a platform which gives you the best results in building and formatting your resume suiting your requirements as per the set templates or patterns. We specialise in formatting your resume in such a way that you do not need to rethink about it. The attraction in the resume is clear through the calls that you get after submitting the resume.
1 note
·
View note
Text
A few things to check when looking at a web application
From: https://twitter.com/rhynorater/status/1585640808568348674
How is CSRF protection implemented? Does the application use only application/json content-type? Can you convert {"name":"Justin"} to name=Justin and change the content-type? Is CSRF token tied to account? Session? Are there any "unauthed" CSRF tokens?
Can you switch POST -> GET? If not, what are you getting? If 405, then it is parsing the route, but GET is disallowed at this endpoint. Try other endpoints.
Is caching implemented? If so, is it tied to certain paths such as /assets? Can you path traverse - /assets/..;/test - does that cache? Can you find a place where HTML content-type will be cached? Try to %3f.css or %23.css trick to see if you can trick the caching mechanism
Sometimes it's as simple as adding ?.png at the end of a URL. In such cases it is often very possible to get web cache deception.
How is information passed between various parts of the system (different domains, etc)? Does the system pass codes via query parameters? URL Fragments? PostMessage? Are there any pages where the X-frame-options header is mysteriously missing?
Cross-domain interactions are almost always sketchy. Look deep into how each piece of these systems is implemented and try to wiggle your way in-between the pieces.
How do all the pieces of authentication work? Is the application using cookies? Auth tokens in the headers? Both? Where do these values appear? I often use the Burp Plugin RequestMinimizer to help identify which pieces of the request are actually essential.
Are there any half-authenticated states? 2-FA not verified states? States before your email/phone is verified? Is authentication ever based solely off of text (such as an email in a JWT token vs an ID)? If so, are there Unicode normalization attacks here?
Is there any documentation for this application? I have legit never regretted reading the documentation for an application. I ALWAYS get something valuable out of it. It takes at MAX 1 hour (most of the time) and you walk away with a much better understanding of the app.
So much of web application hacking is about finding funky states you can get the application into. Reading the documentation will help you understand which parts of the application you (and thus other hackers) have not seen yet, and how to get to them. Priceless.
0 notes
Text
Agobot dos download

AGOBOT DOS DOWNLOAD UPDATE
The spammer uses the “download” command to downloadĪnd execute a SOCKSv4/v5 server. But other options to send spam are possible: So far, SDBot does not implement dedicated spamming O (download|dl) ] ] ]ĭownloads list with email-addresses to spam them O The same commands are also available via FTP can be one of webdav ntpass netbios dcom135 dcom445 dcom1025 dcom2 iis5ssl mssql beagle1 beagle2 mydoom lsass_445 lsass_139 optix upnp netdevil DameWare kuang2 sub7 If given with port, just tries to exploit the host with the scanners fitting the ports, else all scanners are used. Replys stats about exploitings per scanner Removes all netranges from scanner and adds local LAN as scanning rangeĪnubis Bagle CPanel DCOM DCOM2 Doom DW Ethereal HTTP Locator LSASS NetBios Optix SQL UPNP WKS O scan.listnetrangeslist scanned netranges If “recursive” is set, the bot parses the replies and follows This is real nasty since it fetches websites from a webserver. * on the same ethernet segment gives best effects. * filtering enabled – tests with source and destination host * Some of these packets might not pass through routers with for stability and reactions to unexpected packets. * Useful for testing IP stacks, routers, firewalls, NIDS, * routing flags, and other unknown/unexpected packet values. * packet size, header values, options, offsets, tcp segments, * to generate attacks using invalid fragmentation, protocol, * Sends combinations of uncommon IP packets to hosts * IP stack penetration tool / ‘exploit generator’ Implements the well known DDoS attack Mixter authored in 1999. Presenting all the commands is beyond the scope of this paper, as Agobot comes along with over 90 commands in the default configuration. In the following, we cover the more popular commands implemented in the common bots we have captured in the wild. Hopefully comprehensible and applicable port sequences do emerge that can help distinguish extremely well programmed Bots and allow for further study into the most elite Botnets. This activity would have to be monitored during a live session with an intrusive Bot facing massive disconnections and reopening of ports. I have not yet seen enough satisfying data on this topic, although scanning mechanisms and “most frequent port lists” are known, I want to determine if any of the Bots are intelligent enough to connect to more stable ports by either randomly selecting ports to attempt connection or by algorithmic sequencing. A second realm in which I tend to gather data is on the various bots ability to remain connected while various port configurations are enacted. Of course the desires and objectives of each given party are different and thus configurations based on acquired data would be user specific. Research in this realm could also make for more predictable server stability in the long run by providing data for optimized server updating schedules. If a trend emerges in the data gathered that can accurately predict what type of bot is most likely going to connect to which one of your ports and with what command, a much tighter filter can be placed allowing for administrators to better capture the Botnet types they desire to study.
AGOBOT DOS DOWNLOAD UPDATE
Research in this realm should be very conducive towards better arming It personnel in that more effective IDS and IPS systems can be implemented if network admins are more knowledgeable about the evolution, and progressive algorithm enhancement of various bots categorized by attack type, cloning strategy, host IP ranges, lifespan, and update cycle. Having looked at the current research and the various advances and deficits, I am greatly considering looking into the updating behavior and cycles of various Botnets. I think that given the time frame and desire to produce admirable results (having to complete a background check I can not yet deploy a Honeynet on University property, this should be accomplished by the middle of next week). A good look into the basic configurations and commands for three common Bots.

0 notes
Text
[Media] email-header-analyzer
email-header-analyzer E-Mail header analyzer is a tool written in flask for parsing email headers and converting them to a human readable format and it also can: ▫️ Identify hop delays. ▫️ Identify the source of the email. ▫️ Identify hop country. https://github.com/cyberdefenders/email-header-analyzer

0 notes
Text
How DMARC can assist in the prevention of malicious email attacks

DMARC is a widely-adopted email security standard that helps prevent malicious email attacks. Used by over 80% of the world's largest brands, it provides stronger protection against rogue email and limits the spread of fraudulent emails. Domain-based Message Authentication, Reporting & Conformance (DMARC) standardizes and backs up reporting on email authentication and content. It offers a simple, flexible, low-cost method for achieving broad interoperability of different email authentication systems and technologies as well as insight into the email sending practices of your own domains. From the moment DMARC was released, organizations wanted to know why they should adopt it. In this session, you'll get an introduction to the concepts behind DMARC and then dive deep into what it is, what it isn't and how it can be used for your specific organization.
The case for DMARC
Email fraud destroys brand reputation and consumer trust while costing organizations billions of dollars, elevating email fraud to a board-level conversation. Low volume, highly targeted business email compromise (BEC) and email account compromise (EAC) scams are the most dangerous—even more costly than ransomware.
The Digital Marketing email ecosystem is under siege. Cyber-criminals have found innovative ways to monetize and maximize their return on investment through email fraud, (BEC) business email compromise and (EAC) email account compromise scams. From a consumer perspective, these fraudulent emails are confusing and craftily designed to manipulate and deceive. Fraudsters steal millions of dollars every year through BEC and EACs.
Read Also: What is Business Email Compromise (BEC)?
This white paper explores how applying DMARC to your organization's email infrastructure can significantly lower exposure to both impersonation and account compromise attacks, and the benefits of the new DMARC policy assertions to aid reporting. Effective BEC strategies require a combination of technical, operational and human processes using a layered approach. DMARC is the most important of these technical layers, blocking all spoofed emails from reaching your customers, employees and partners. Domain spoofing is one of the methods used by attackers to get an email delivered to a user’s inbox instead of their spam folder. It takes specialized expertise to parse email headers and figure out if mail was spoofed. The easy solution is to adopt DMARC, which allows you to use your own domain as a security measure.
DMARC adoption today
DMARC adoption has continued to grow over the last decade. As of December 2020, 23% of sending domains reject unauthenticated mail, while another 11% of sending domains send mail to quarantine, according to Farsight data published on DMARC. While this data represents continued implementation growth, it also means nearly 80% of domains are still not rejecting unauthenticated mail. For the last decade, DMARC has been available as an option for email protection. In the last year, more than a million domains have adopted DMARC.
DMARC hazards
Organizations choosing to navigate the DMARC journey—without outside assistance—using internal resources need not stumble without proper tools. To avoid doing this, there are a few hands-off tools you can use as well as some tips. This research brief will help you get started on a successful DMARC journey. It describes common pitfalls as well as important prerequisite steps. It then presents a six-step checklist to build a data management system and stay on the DMARC journey. Finally, it provides tools and references to help organizations stay on track.
As the security teams decides whether or not to deploy DMARC to protect its trusted domains, there are several potential hazards team members should know about:
· The high risk of blocking legitimate mail.
· DMARC requires extensive expertise.
· How to store, render, and analyze large data sets.
· A process for identifying and contacting stakeholders.
· Ongoing support and management.
Take the DMARC journey
Our experts will discuss the continued threats of email fraud and explain why it is essential to implement and enforce a robust, company-wide email authentication policy. Email fraud has become a 360-degree problem, as criminals can leverage multiple identity deception tactics to target various stakeholders involved with an organization. This tends to include their employees, customers, and business partners, so mitigating these potential hazards should become a high priority. Consider these four steps to kick off your journey:
· Select a domain. Consider a sub domain vs. primary domain to get started.
· Enable monitoring. Set the mail receiver policy to “none.”
· Add the DMARC Record to DNS. Use the organization’s standard DNS addition process.
· Receive and analyze domain reports. Starting with one domain will reduce the noise.
DMARC provides a powerful benefit to a customer’s messaging ecosystem. As with any complex technology, it’s necessary to start small and plan the implementation in phases. The Take the Best DMARC Solutions Journey customer retention plan includes instructions for starting your journey toward a fraud-free messaging ecosystem. Resources are available for defining objectives, identifying resources, creating and executing a plan, putting in place a monitoring strategy, and more. Ensuring that an organization’s email infrastructure is properly configured to reject or quarantine messages based on DMARC policy will reduce the volume of spam and phishing emails received by employees. The email fraud landscape is changing. In order to dramatically reduce the number of fraudulent emails sent to consumers, businesses and government organizations, DMARC provides a critical system for validating that messages are authentic.
Source : https://medium.com/@aariyagoel5621/how-dmarc-can-assist-in-the-prevention-of-malicious-email-attacks-a3510f061232
0 notes
Text
The Role of DMARC in preventing Phishing
Introduction
We’ve all heard a lot about phishing and how attackers steal money and data from gullible users. The impact is huge. You might wonder. How do we get rid of this menace? How do we keep our emails safe? How do we ensure that our emails are used by just us and not somebody else?
We have an answer for all your questions: DMARC!
DMARC for Dummies
DMARC (Domain-Based Message Authentication, Reporting, and Conformance) is a standard or system for determining whether or not an email is legitimate. It uses SPF and DKIM, two additional protocols, to determine an email's authentication state. DMARC allows organizations to see who is sending emails from their domain, improves email delivery, and, most critically, protects against domain spoofing, phishing, and impersonation threats.
If your company's domain name is mycompanyisthebest.com, you don't want a cyber attacker to be able to send emails from that address. This jeopardizes your brand's reputation and has the ability to propagate financial malware. The DMARC standard avoids this by verifying that emails are being sent from the expected IP address or domain. It defines how domains should be informed if there are difficulties with authentication or migration, and it gives forensic information so that senders may monitor email traffic and quarantine suspicious emails.
Now you might ask why would you need DMARC specifically?
Why DMARC?
Well, firewalls and Internet security software, for example, are insufficient to guard against email phishing attacks. To strengthen your security, you must first understand how your firm communicates via email. This necessitates the use of advanced techniques, such as professional email forensics software. These programs can help you parse and analyze every email that your company sends and receives in order to identify potential email phishing attempts and mitigate damage even if an attack has already happened. However, before you do so, you should think about implementing easily available email security standards like DMARC, SPF, DKIM, and DMARC is the best option available to safeguard your incoming and outgoing emails.
Identifying a Phishing Attack
The threat of spoofing is not new. Email spoofing is a misleading technique used by attackers to modify both the identity of the sender and the seeming origin of email communication. The majority of spoofing attacks employ falsified header information or construct a bogus sender email address.
Recipients can detect phishing emails sent from a faked firm domain by inspecting the email header information, such as the "from:" and "return-path" addresses, and ensuring that they match. While the email "From" address is normally accessible in the header, the "return-path" address is not always visible, and upon inspection, it might assist receivers to determine the original identity of the attacker.
Stop Email Phishing Using DMARC
To let DMARC handle all security checks for your email communications, you need to set up the policy of p=reject. It is an effective solution in countering a wide range of assaults, such as direct-domain spoofing and email phishing.
DMARC assists in verifying the origin of emails and preventing bogus emails from being received and opened. However, only a tiny number of firms have embraced the protocol, and an even fewer number of them have done it successfully.
EmailAuth's DMARC analyzer assists businesses in attaining proper DMARC enforcement! While ignoring a DMARC reject policy might result in the loss of genuine emails, hosted DMARC services assure improved email deliverability and fewer email phishing assaults over time.
EmailAuth's DMARC analyzer assists enterprises in securely upgrading their DMARC policy from monitoring only to p=reject, allowing them to reap the advantages of email authentication without fear of repercussions.
Furthermore, while you are on p=reject, you may take advantage of BIMI's visual identification benefits by attaching your distinctive brand logo to certain outgoing emails that reach your clients.
Original source: https://www.reddit.com/user/emailauth-io/comments/tatkpk/the_role_of_dmarc_in_preventing_phishing/
0 notes
Text
Different Queries Related to Google’s Mobile Friendly Update
Google’s mobile friendly update has been aired, and several sources have got some reliable information regarding this. Nine such key points concerning Google’s mobile friendly update are as follow: Changes made by Google to its algorithm on 21st April Google has been bringing lots of changes to different apps recently. Google Play, which is the presentation of mobile SERPS, and some more advanced development guidelines that have an impact on mobiles are believed to be in preparation for the 4/21 update. We, as of now, have no advanced clue about the changes that will be announced by Google on 4/21 but on the basis of our observations points mentioned, below is our best guess. Our assumptions say that Google is going to launch a new mobile crawler that will be better at crawling single-page web apps, Android apps and even deep links in iOS apps. As Android has been built in Java, the new mobile-friendly guidelines launched last month focus mainly on JS and CSS. Single-page web-apps rely heavily on JavaScript for their fluid experience. Sites that use Responsive Design well in single-page app architecture are as follow: • Refinery29.com • Hullu.com • Techcrunch.com • The Google Play Store • Facebook’s news feed • Pinterest.com A new mobile-only index to complement the new crawler also makes sense because Google wants to index and rank app content and deep links to screens in apps. We also assume that the recent increased focus on deep links coupled with the announcement of the new Google Play’s automated and manual review process are related. We can thus say that Google has created a crawler that is capable of crawling Android apps. It is also very surprising that Google has not focused more on mobile page speed in terms of the announcement of the mobile-friendly initiative. Are desktop-rankings dependent on the mobile-friendliness of the site? No is the answer to the aforesaid question answered without any hesitation on a panel at SMX Munich, Zineb from Google. New index related to a new crawler and/or a major change to the infrastructure they are using to index, evaluate and parse mobile search results but not desktop results are considered as another indication. Measure of the impact on mobile rankings: On the panel at SMX Munich, Zenib said that this change on 4/21 will be bigger than the Panda and Penguin updates. We believe that this fits with the change in the infrastructure. It is still not clear if all the mobile devices will be impacted by this change. It is still unclear how the change is expected to impact Android and iOS devices. Some differences have been observed the changes on types of search results seem more significant on Android than iOS. E-mails are also impacting SERPs increasingly since mobile email opens have grown up by 180% in three years and Google, simultaneously, is trying to take advantage of this increased engagement of mobile devices. But inclusions like these may help you with the maintenance of the keyword rankings in the mobile search after April 21st but it may not necessarily help you with the sustenance of mobile traffic. Sites that redirect to a mobile sub-domain and their friendliness: This is a very growing and interesting topic to talk about as we can see the significant websites ranking well in mobile SERPS. It’s almost like counting the mobile sub domain as a Mobile-Friendly signal. It is interesting to note that many Google representatives have recently backed off of their strong insistence on responsive design. It is still believed to be the least error-prone and easiest to crawl and index. How will you know if your site meets Google’s requirements for mobile friendliness? Google has made a mobile-friendliness tool that will give you a ‘yes’ or ‘no’ answer on a per-url basis. Evaluation of pages is done individually, so doing a site query for the domain in question on your phone is another way to get a sense of how your top pages perform. This will ensure you see all pages indexed to the domain and will also help in evaluating which one should be considered as mobile-friendly, without submitting them to the tool one at a time. This has already been declared by Google that mobile-friendly test results are binary i.e. the answer is either they are or they are not. But we have discovered that the tool result does not necessarily always match up with what we see on our phones. Impact of having a mobile app on my mobile rankings: There are two things which should be taken into account over here. First is, if a mobile search query is highly correlated with mobile app listings, your app could see more visibility within mobile search results pages. This is because Google has initiated treating apps as a new kind of universal search result. They are introducing an “App Pack” for Google Play results for searches on Android devices and adding a drop-down to the main nav-bar on iOS devices. An “App-Pack" is a group of related apps that rank together for a given query. It has different formatting and an App headers. These often rise to the top of a mobile search result. Apps with keyword-optimised titles and have quality ratings and reviews could jump to the top of the mobile web SERPs if Google starts to serve these App Packs on iOS device searches as well. Second is the consideration of high-quality apps to be a positive ranking factor in mobile search by Google. This is taken as to mean the deep links between your website and your app will improve your website rankings in mobile search. Are apps like Android, iOS or both necessary? What if the budget is very limited? There can be significant value to maintaining both if you have the budget to develop both a mobile app and a mobile website. If the budget is limited, then you need to decide but the decision should be on the basis of the business and not on SEO. Apps are, no doubt, riskier as they require more up-front investment and have to adhere to App Store guidelines and approval processes that are not in your control. If the decision is in the favour of apps, you can use the OS data in Google Analytics which will help you in determining which OS is more popular among users. If this data is not with you because you don’t have a website yet, or you have a limited mobile audience to choose a trend, you should go with the option in which matches with your monetisation strategies. Impact on mobile traffic by the user search query and a solution to the way of keeping our desktop or mobile keywords as our top keywords: Google is trying to do a much better job of embracing a user’s intent from the query. Google has expanded the types of information that they scrape and pull from a site directly into an answer box i.e. a mobile, usually. The number of aggregator-style sponsored results that can be seen on mobiles has also been increased and diversified by them. In terms of the importance of the keywords, it can be a tough nut to crack. It is not that easy to find out which ones are more mobile-oriented than desktop oriented. Some of the sophisticated solutions are those from Search Metrics and Bright edge. Google’s goals for initiating all of these mobile-friendly changes: There are many issues for which Google has decided to take this initiative. But the prime reason for making these changes is to provide a better experience with the mobiles for searchers and give people exactly what they want. Yes of course, this can be for money-making as well. Google has also been encouraging the publishers to include transcripts with videos and song lyrics with songs. This will be very beneficial for the Google scrape in the long run. You all will be able to download any songs or videos directly to your phone on Google Play. These are the goals of the Google shortly described over here. However, we expect this to expand more in future so that Google can expand their level of competitiveness as well. Read the full article
1 note
·
View note
Text
How to Monitor Exchange and Office 365 Mail Queues

How to Monitor Office 365 Mail Queues and Troubleshoot Slow Email Delivery for Exchange and Exchange Online
I am sure you’re having exchange mail queues issues, right?
Despite the recurring predictions for its death, businesses of all sizes still run on email. Yes, messaging and news feeds like Yammer and Slack have a place in corporate collaboration. But the asynchronous nature of email is what makes it adaptable and robust. This asynchronous delivery is critical to make email robust and scalable. It also makes it exceedingly difficult to continuously monitor.
On top of this, most corporate email systems employ additional layers and filtering including external cloud-based SMTP Filters and spam protection. These extra layers add points of failures and latencies for both inbound and outbound mail flow. To add to an already complex picture — Office 365 has its own message queueing systems.
But when everything was behind the firewall, it was easy enough to detect stuck mail queues and resolve the situation. Now with cloud-based systems like Office 365 and Google Apps, it’s nearly impossible to monitor what’s working and what isn’t — unless you are using CloudReady, of course.
Watch our latest video on monitoring Microsoft Exchange Online performance
Watch this video to learn how to Monitor Microsoft 365 Exchange Online Mail queues, SPAM filters, and troubleshoot slow…
How To Monitor Exchange Online
www.exoprise.com
How CloudReady Monitors Mail Queue Performance
CloudReady has invested considerable time and effort in developing our email sensors to solve just this problem. All of the CloudReady Email Sensors including Exchange Online, Hosted Exchange, Outlook Web App, IMAP, Gmail, and On-Premise Email (MAPI) sensors send synthetic emails between the mail platform and our auto-responders. We knew from the beginning that testing email delivery, reliability and performance was critical to our customers confidence in the cloud.
How Does It Work?
All of our CloudReady sensors exercise the entire email system by sending a small test message from the sensor to our cloud auto-responders. When the sensor is browser-based, Gmail or Outlook Web App (OWA) for example, the sensor will navigate through the product to generate a test message just like a real user would — opening dialogs, hitting compose buttons, etc. Exoprise emulates a real user utilizing the product end-to-end and monitoring the whole experience. For reliable and accurate monitoring, a simple API test won’t get the job done.
Once an email is generated, our sensors confirm that the message was sent by checking the appropriate folders and headers on the outbound/sent side. Until then, we start the wait for the reply. Additionally, for many of our sensors, we set up mailbox rules to hide our synthetic emails. We do this so that customers can re-use existing accounts for monitoring email systems. Also, they can get maximum coverage across their mailbox servers or Database Availability Groups (DAGs).
Next, we wait for the reply from our auto-responders so that we can parse up the timestamps, the MIME and extended header data, and report on the success or failure of the transmission. Our sensors have an exponential back-off algorithm and will wait up to approximately 3 minutes for a reply. We figure if the systems and layers can’t get a small email out and back within 3 minutes then its going to be too slow with real content and we report a failure. We’ve tested these thresholds with our customers and our crowd-powered data (see below).
Time Synchronization
If CloudReady is to measure the timings of interactions and round-trip times of emails, a good source of synchronized time is required. Unfortunately, CloudReady can’t guarantee that a customer system has a reliable clock or that it is kept time-synchronized. Therefore, a CloudReady installation has to periodically synchronize its own concept of time to our servers and use that time source for its measurements.
We use this time synchronization across many of our sensors so its well worth the effort for improved accuracy.
Super-fast Auto-responders
Exoprise leverages a node-based SMTP application, haraka, to process its messages as a well as series of custom plugins. You can read more about haraka here. Since its node-based its event driven, incredibly fast, and highly scable. Our auto-responders process 100’s of thousands of inbound and outbound messages each day, typically in < 10 milliseconds per each message.
See How Microsoft Office 365 Has Been Performing
Subscribe to our weekly report to see the performance and availability trends of Office 365. These statistics are measured by anonymously aggregating data from our CloudReady customers and measure real uptime from 1000’s of locations throughout the world.
SUBSCRIBE TODAY
Continuous measurements: Inbound, Outbound, and Transport Times
CloudReady continuously captures a number of metrics related to Message Queue performance and we are expanding this data-set all the time:
MTA Outbound Time The time it takes to send an email to our CloudReady auto-responders. This metric measures outbound queue and transfer performance. MTA stands for message-transfer-agent and is responsible for the transmission of the email between servers.
MTA Transport Time The time it takes for a reply to reach the inbound MTA servers. This metric measures inbound transport performance and is a subset of the MTA Inbound time as reported by processing servers.
MTA Inbound Time The total time it takes to reply to an email from our auto-responders to the inbox. This metric measures inbound queue performance.
MTA Queue Statistics without Crowd Comparison
How to Interpret the Results
Let’s look at each one of them
MTA Outbound Time
A large MTA Outbound Time likely points to your outbound SMTP filters and/or the providers or on-premise Exchange mail queues that are having problems.
MTA Inbound Time
When you have a large MTA Inbound Time but no corresponding MTA Transport Time then you have a stuck inbound mail processing queue problem. If its an Exchange or email environment within your control then you should consider increasing the resources for your inbound queues.
MTA Transport Time
Ok, so you have a large MTA Transport Time then you have a problem with your SPAM or AV processing. Typically, this is the culprit and the source of the slow mail replies. When you see large MTA Transport Times — upwards of 3 or 4 minutes to process a small 900-byte message — you can guarantee that you will have a problem with email delivery in the future. Larger messages with attachments will take even longer to process.
Crowd-powered Like the Rest of Our Statistics
Just like ALL of the metrics that Exoprise CloudReady collects, we crowd-source our MTA statistics. That way our customers can understand what is typical for inbound and outbound mail processing. Being able to do this comparison across on-premise Exchange servers and Office 365 environments is very helpful in evaluating a migration to different SMTP or SPAM services.
We have had customers come to us and say “we thought our email was slow, we just didn’t realize how bad it was until we could compare it to other systems”. That is the power of CloudReady crowd-powered monitoring.
Bad MTA Filters and SPAM Protection Without Crowd Compare
Find out if you have an Office 365 mail queue problem today
CloudReady is a simple and powerful way for customers to get insight into and monitor their critical email flow. Don’t wait until after an outage to know whether or not you received that crucial proposal, purchase order, or support request.
Start a Free Trial Today. Its Simple To Get Started
Every day customers start and deploy a full suite of sensors in under 5 minutes. Give it a try for network benchmarks, root cause analysis and complete visibility into ALL of Office 365.
FREE TRIAL
0 notes